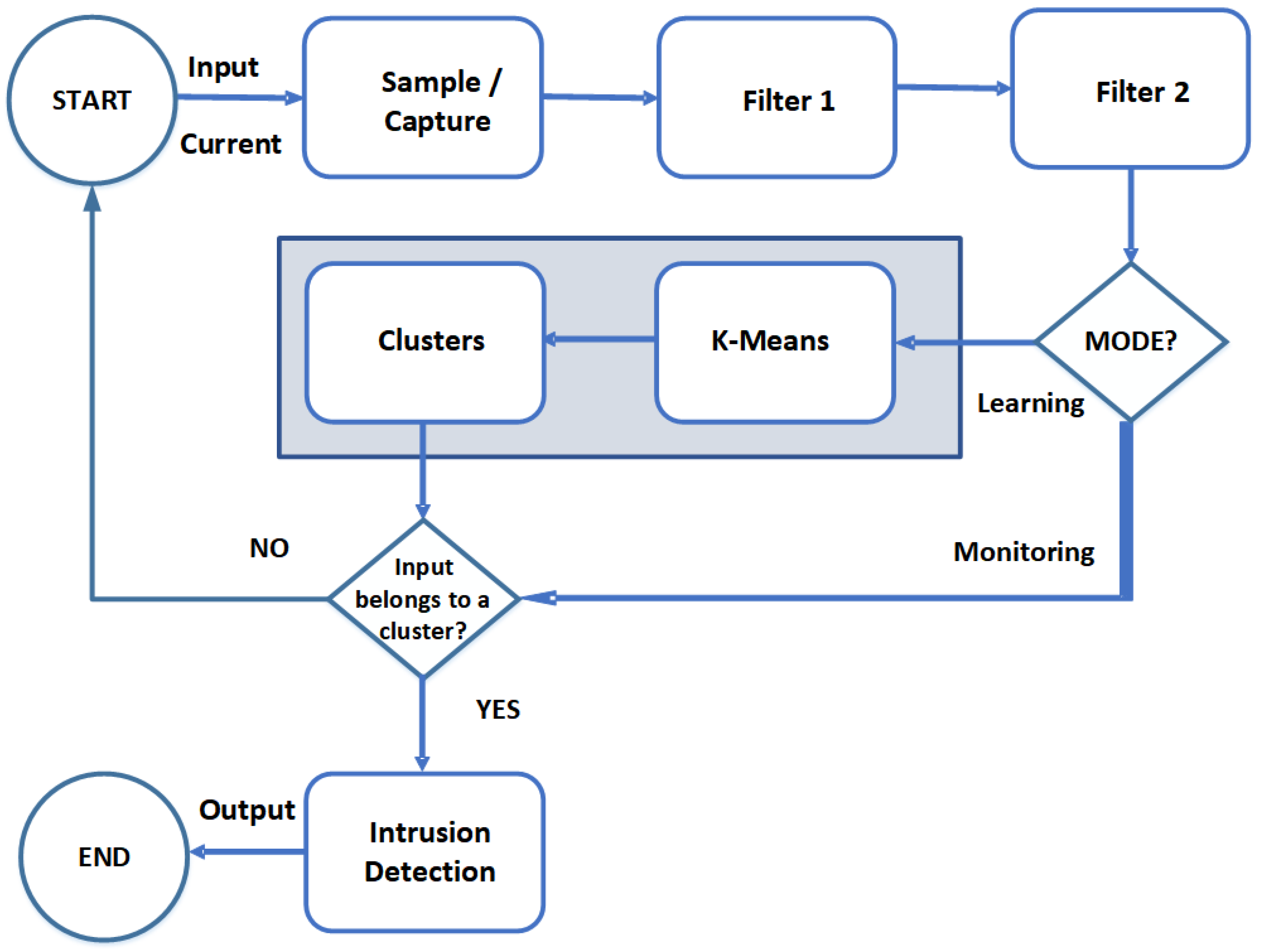
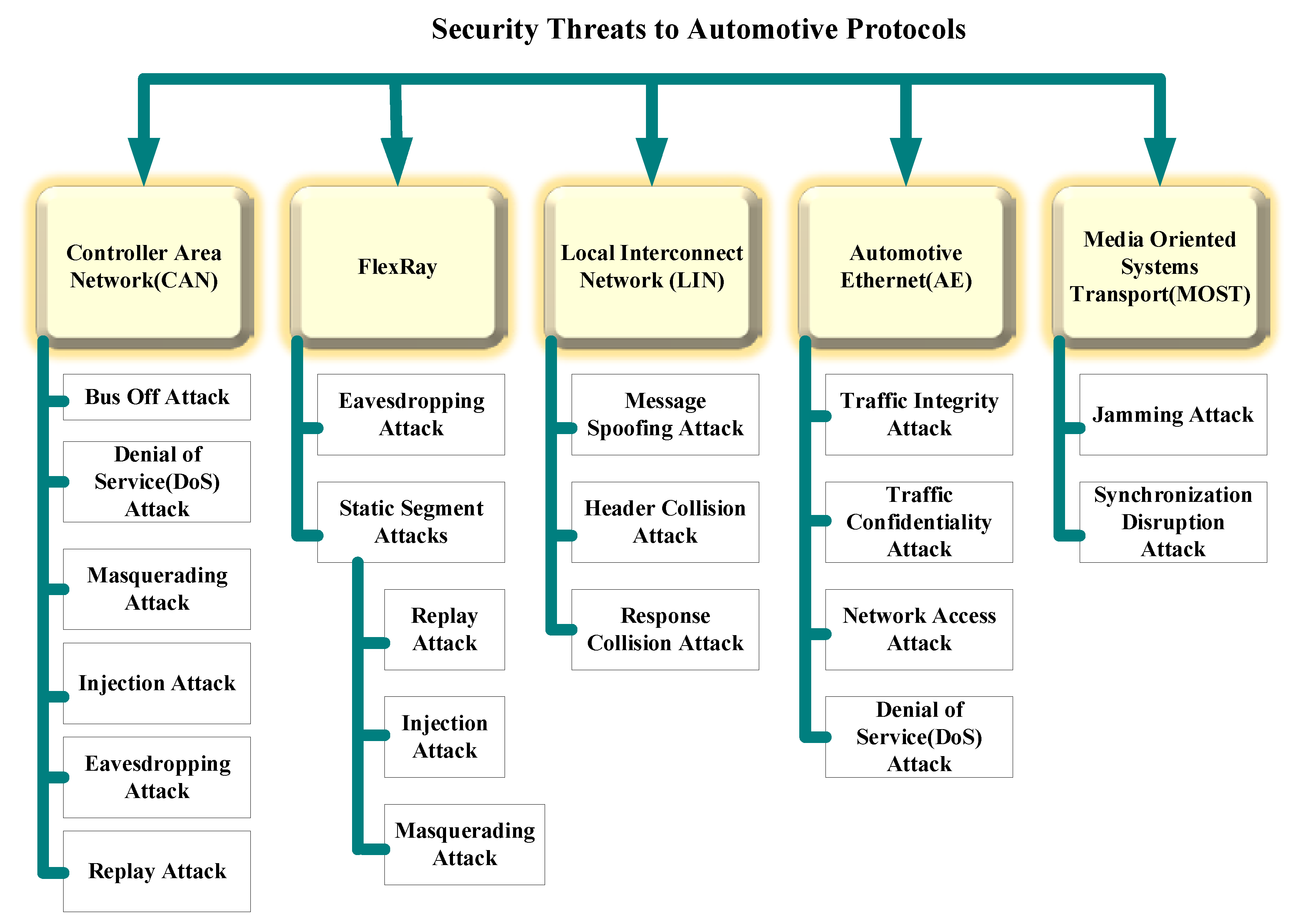
Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review

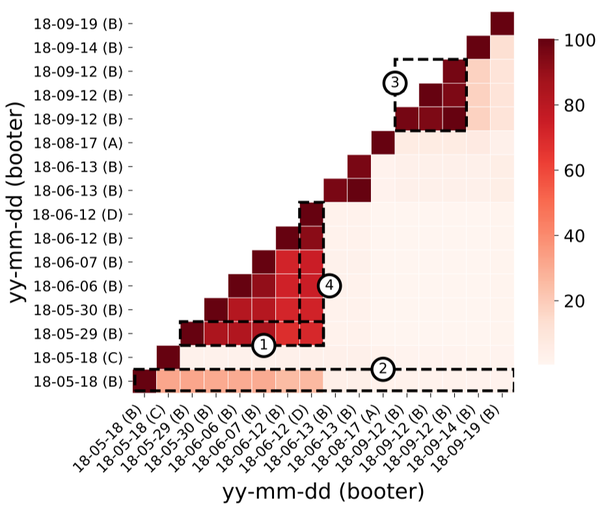
A detailed survey of denial of service for IoT and multimedia systems: Past, present and futuristic development | SpringerLink

A detailed survey of denial of service for IoT and multimedia systems: Past, present and futuristic development | SpringerLink

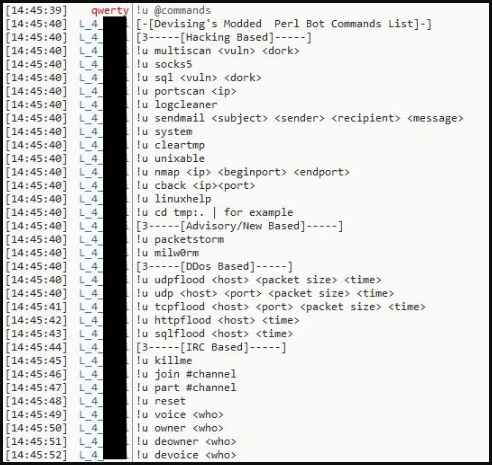
PDF) IoDDoS — The Internet of Distributed Denial of Service Attacks: A Case Study of the Mirai Malware and IoT-Based Botnets






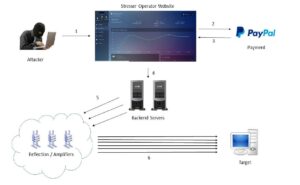
![TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube](https://i.ytimg.com/vi/iwYldG8VYsY/maxresdefault.jpg)